
An Innovative Partner in Retailing
ESG
Reliable Information Security and Protection
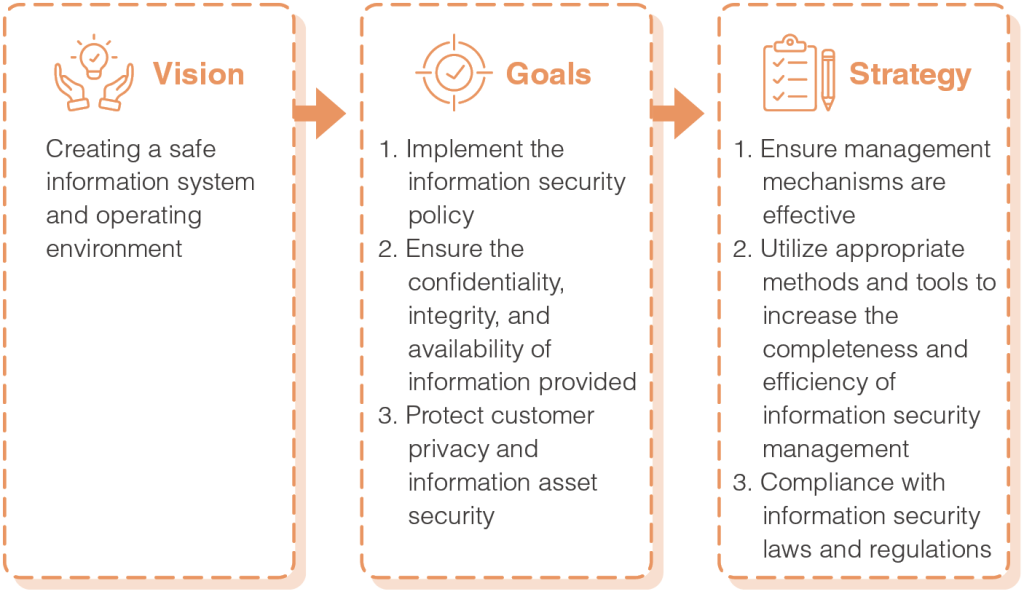
PChome is committed to providing secure and robust online shopping environments to customers through continuous system optimization and improved user friendliness. In addition to protecting consumption information relating to our customers, we also regard individual privacy highly as a fundamental assurance. The number of cyberattacks has increased along with growing demand on online shopping, and PChome prevents any potential information security risks through its internal structure, risk assessment, and system upgrade. We continue to strengthen our defense-in-depth measures to reduce the likelihood of business interruptions caused by hacker attacks; continue to optimize malicious activity detection mechanisms, increase the efficiency and response speed, effectively contain, and minimize the scope impacted by such activities; continue to increase information security training sessions and social engineering drills, and periodically inspect the information system according to the Company’s information security policy and implementation regulations. PChome will maintain the strictest standards to face even more severe information security challenges in the future, and create a safe information system and operating environment to protect consumers’ rights and interests.
Information Security Governance Structure
The Company established a dedicated cyber information security office department in 2018 to strengthen information security management and establish a trustworthy information application system and environment. A central management unit is established under the office department to oversee the group’s establishment of information security and protection related policies, implementation, risk assessment, control, and compliance audits, in order to improve information security and service quality for online services, making PChome an online shopping platform that consumers can feel at ease using. Consumers do not need to worry about information security or their personal privacy being invaded. This ensures our operating ability and information service performance. The highest level supervisor of the Cyber Information Security Office department periodically reports information security management results, related issues, and directions to the CEO GM and Audit Committee.
To implement the information security strategies devised by the Cyber Information Security Office Department and to ensure internal compliance with information security-related practices, processes, and regulations, we established an Information Security Task Force. The CEO GM assigns an information security officer to serve as the convener. Members are responsible for the protection, audit, governance, and crisis management of information security-related affairs. Additionally, senior-level managers from all business units form an information security implementation task force to carry out policy implementation tasks. The executive secretary is responsible for organizing meetings, coordinating safety affairs, and carrying out information security training. Meetings are convened on a quarterly basis to review and decide the relevant solutions and policies on information security and personal data protection, and to ensure the effectiveness of our management measures.
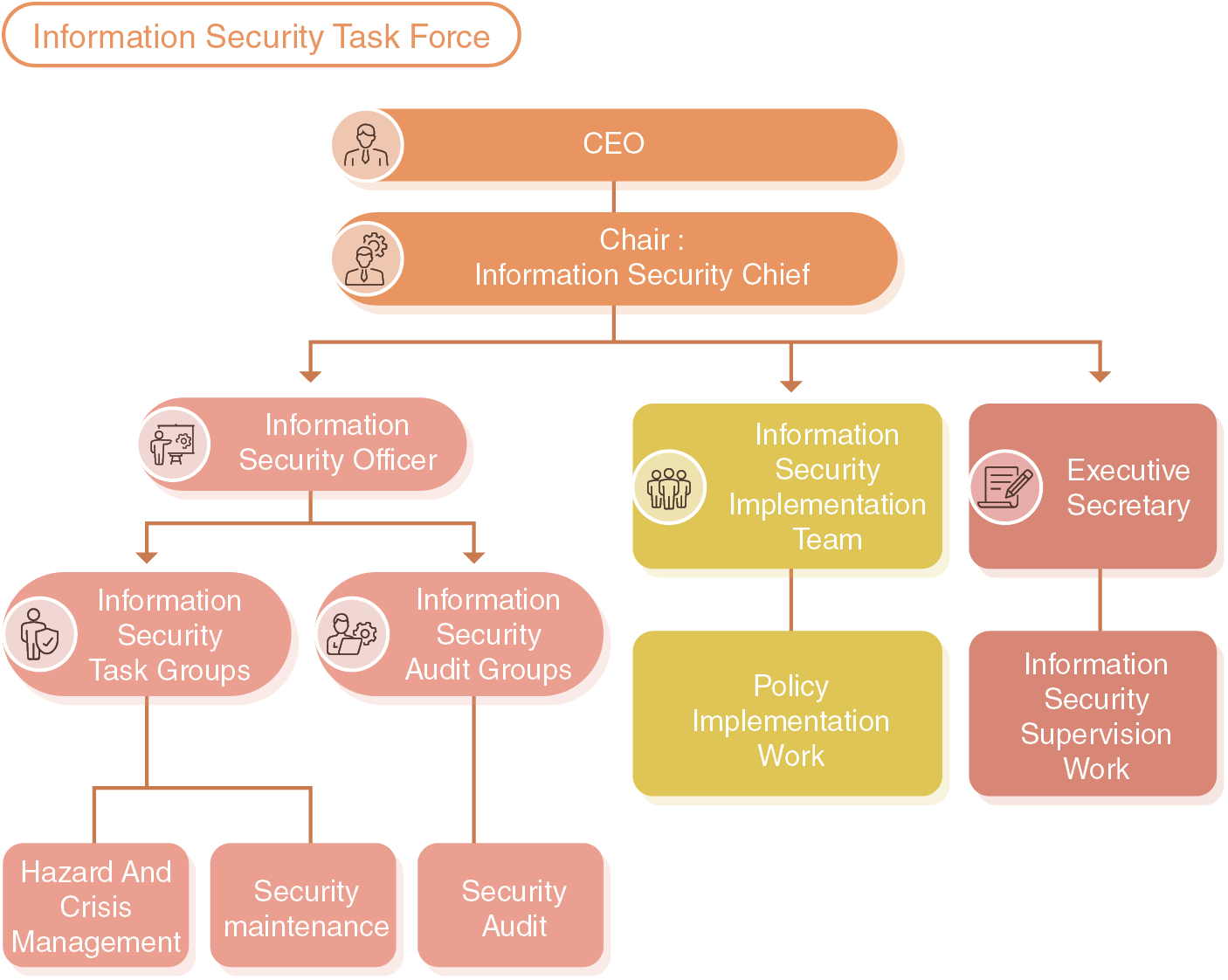
Information Security Measures
PChome established a comprehensive information security management policy to enhance information security precautions and implement concrete measures. We assess information security risks from the perspective of system, technology, and procedure, and set the priority of risks based on the risk level, probability of occurrence, impact, and cost required to avoid the risk. We clearly identify major risks that will impact our business and information security, and utilize the PDCA (Plan-Do-Check-Act) management approach to ensure that risks are effectively lowered, thereby establishing the highest level confidential information protection services that meet customer needs.
We have also established multiple layers of information security measures, and continue to adopt information security defense technologies, establishing information security monitoring and maintenance mechanisms that include identify, protect, detect, respond, and recover. We established a supplier risk management process to control risks in various aspects and protect the Company’s important assets, such as the confidentiality, completeness, and availability of personal data, trade secrets, and online services.
PChome also actively monitors information security management results, and carries out information security risk assessment, analysis, and improvement measures based on internal information security inspection results. We conduct a variety of information security drills to ensure our ability to defend against attacks, and systematically raise the information security awareness and alertness of every employee, preventing information security risks before they occur. Furthermore, PChome continues to organize an information security general meeting and information security training to raise the informational security awareness and knowledge of all employees, providing information on information security and collecting information security incidents to remind units of matters requiring attention and protection methods. We also irregularly arrange information security training for employees, in order to help employees stay up-to-date on the latest information security trends and knowledge and strengthen their information security ability.
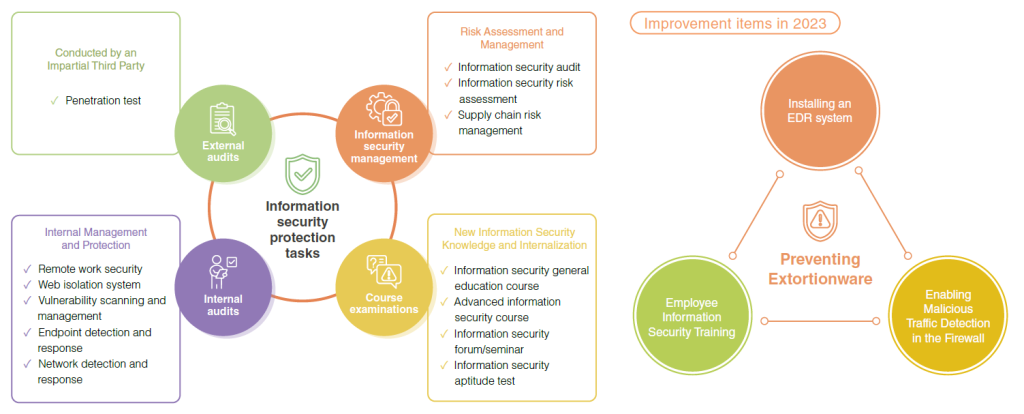
Various information security risks are concomitant with IT developments. PChome has established a comprehensive Internet and computer security protection system that includes access control and information management measures to maintain essential processes such as company operations as well as information security management. Based on our information security risk analysis and assessment, our potential risks mainly come from advanced persistent threats generated by any third-party. To prevent such attacks from stealing our trade secrets, breaching customer data and other confidential information, as well as damaging the rights, interests, and reputation of our company, we
employ the following strategies for active identification and rectification of any potential information security risks:
Methods for Identifying Potential Information Security Risks
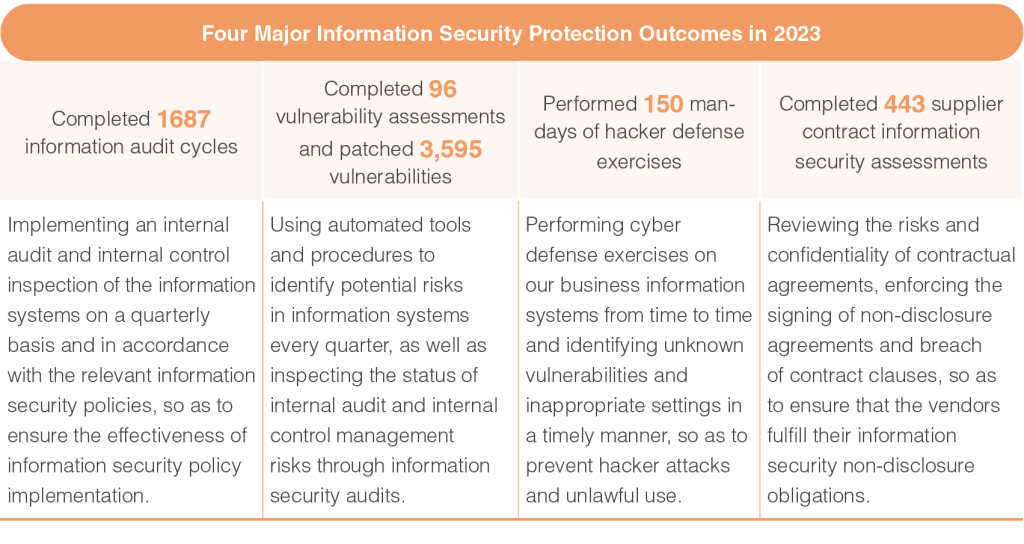
1. Implementing an internal audit and internal control inspection of the information systems on a quarterly basis.
2. Using automated tools and procedures to identify the potential risks in information systems every quarter.
3.Reviewing and evaluating information security-related regulations and procedures annually, so as to ensure their appropriateness and effectiveness.
4. Organizing annual information security audits to mitigate information security risks.
5. Performing cyber defense exercises on our business information systems from time to time.
Methods for Resolving the Identied Potential Information Security Risks
1. Inspecting the status of internal audit and internal control management risks through information security audits, so as to ensure the effectiveness of information security policy implementation.
2. Inspecting the outcomes of the cyber defense exercises performed on our business information systems and identifying unknown vulnerabilities and inappropriate settings, so as to prevent hacker attacks and unlawful use.
3. Performing in-depth investigations on abnormalities in outsourcing contracts to ensure that vendors fulfill their information security non-disclosure obligations.
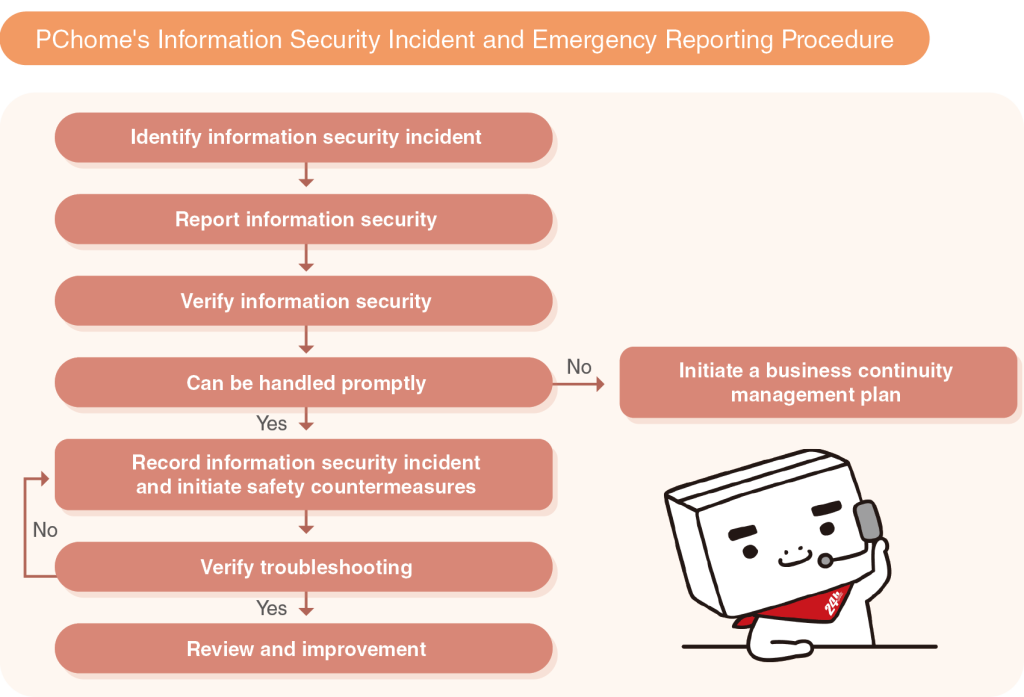
With regard to the process of reporting and handling information security incidents, PChome has devised an incident and emergency reporting procedure that systematically consolidates reporting, interpretation and analysis, treatment, review, and improvement procedures. This ensures that information security incidents are resolved quickly and appropriately and that similar incidents can be prevented in the future. PChome did not experience any incidents of data breach, data loss, or missing customer data in 2023. We shall continue to implement our internal information security strategies to safeguard company information and customer rights and interest.
Information Security Training Program
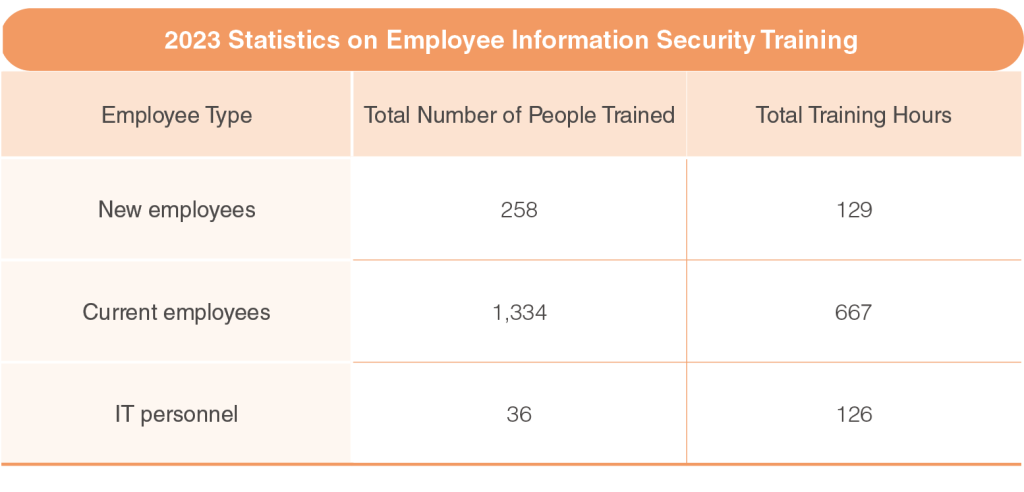
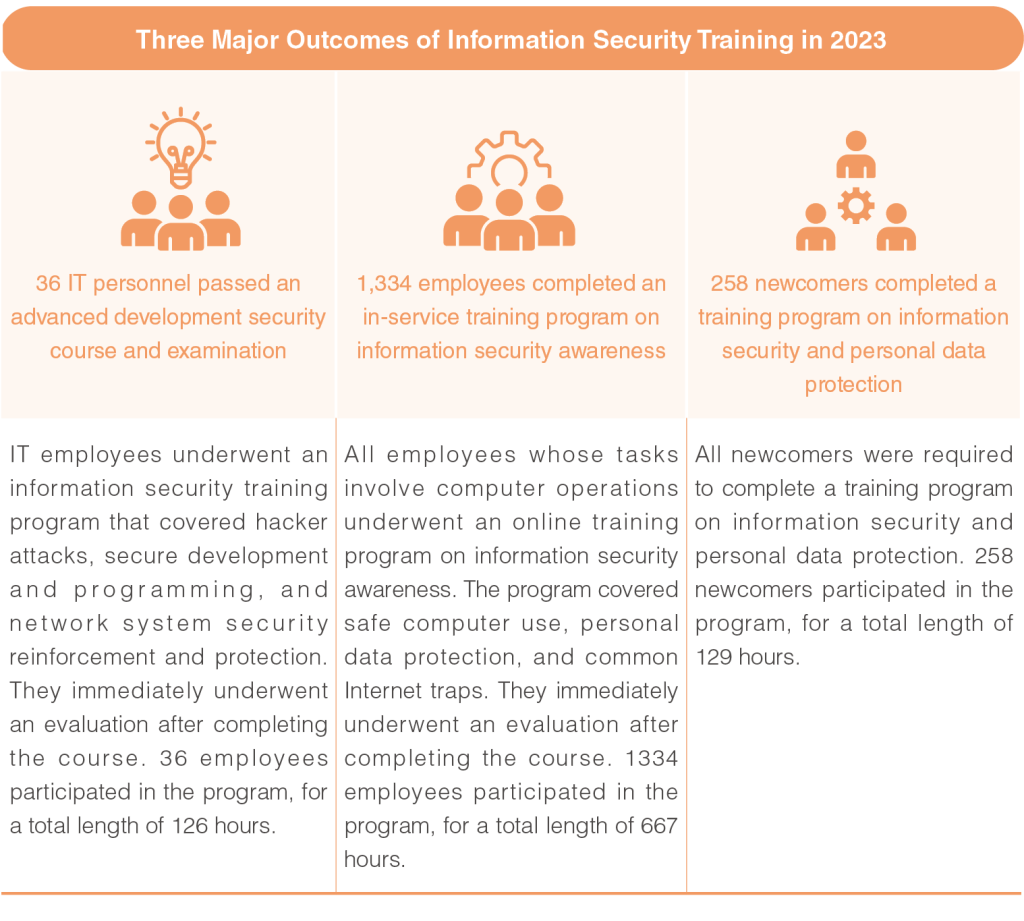
To improve our employees’ awareness and understanding of information security, PChome continues to organize an information security general meeting on a quarterly basis to convey relevant information. At the same time, we follow up on the progress and status of information security tasks in each department, while detailing information security events and news relevant to each department so as to remind them of precautionary measures and defense methods. We also organized external training programs for employees to ensure they are updated with the latest information security-related trends and knowledge this year.

Customer Data Protection
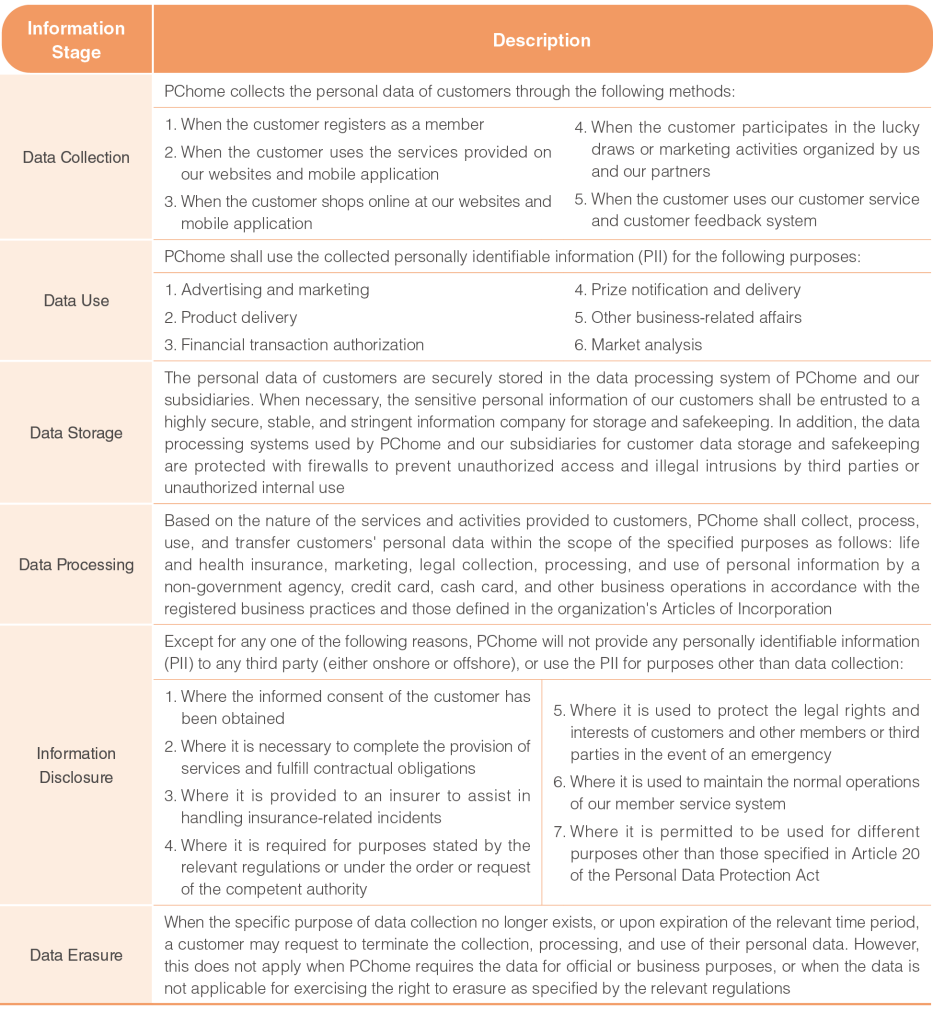
To protect consumer privacy, PChome protects customer data in accordance with our Terms of Service and Privacy Statement. The Privacy Statement and the disclosures therein are applicable only to the websites and mobile applications owned and operated by PChome. PChome will not provide information sufficient to identify a user to any third party (either onshore or offshore), or use the data for any purpose other than the purpose for which it is collected, unless the Company gives prior explanation, or as necessary for the purpose of completing provision of services, or fulfilling contractual obligations, or in accordance with the relevant laws and regulations or as ordered or requested by a competent authority. To this end, no members were involved in the following company activities in 2023: marketing, consumer/customer management and service, providing online shopping and other e-commerce services, protecting the rights and interests of the parties and stakeholders, providing after-sales services, handling reward activities, and engaging in other registered services or services specified in the Articles of Incorporation. Additionally, for the purpose of implementing e-commercerelated business, PChome may collect behavioral customer data and personally identifiable information (PII) based on user registration details and purchase history. We conditionally assess the commercial behaviors conducive to promoting our business activities while complying with information security regulations.
In addition, PChome has defined the relevant regulations for each stage in the information life cycle. For more details, please refer to the PChome Online Inc. Terms of Service and Privacy Statement.
In addition to protecting customer data security and privacy, PChome is also committed to safeguarding Internet safety for children. We offer tips on how to teach children to use the Internet safely and allow children and their parents to protect their security and privacy online. For more information, please refer to our Internet safety guide for children.


.jpg)